- Products
Quantum
Secure the Network IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloudGuard CloudMates
Secure the Cloud CNAPP Cloud Network Security CloudGuard - WAF CloudMates General Talking Cloud Podcast - Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Quantum (Secure the Network)
- CloudGuard CloudMates
- Harmony (Secure Users and Access)
- Infinity Core Services (Collaborative Security Operations & Services)
- Developers
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Infinity Portal
- Products Announcements
- Threat Prevention Blog
- CheckMates for Startups
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
May the 4th (+4)
Roadmap Session and Use Cases for
Cloud Security, SASE, and Email Security
SASE Masters:
Deploying Harmony SASE for a 6,000-Strong Workforce
in a Single Weekend
Paradigm Shifts: Adventures Unleashed!
Capture Your Adventure for a Chance to WIN!
CPX 2024 Content
is Here!
Harmony SaaS
The most advanced prevention
for SaaS-based threats
CheckMates Go:
The Difference Is In The Details
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Quantum
- :
- Security Gateways
- :
- Traffic selector 0.0.0.0/0 in IPSec with CISCO ASA
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Traffic selector 0.0.0.0/0 in IPSec with CISCO ASA
Good morning everyone,
I am setting up IPsec over the Public Internet with many partners around the world. One of my partners uses a Cisco ASA, and there was a problem with that. CheckPoint send traffic selector 0.0.0.0. Cisco rejects the request and IPsec does not up. Has anyone encountered such a problem?
I use CheckPoint 1800 on cluster.
Thanks!
Labels
- Labels:
-
Site to Site VPN
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds like both ends disagree on what the encryption domain is and/or you've configured your end to establish a single tunnel for all traffic (0.0.0.0) and the other end isn't configured to accept this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi PhoneBoy!
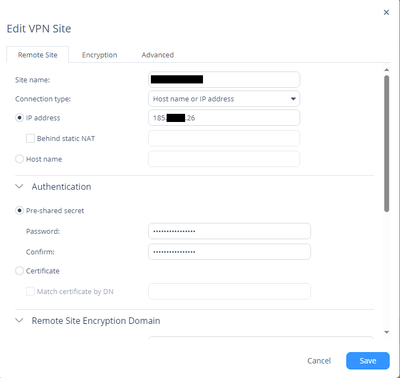
I need configure connection between local network 185.xx.xx.xx/29 (my CP) and 91.xx.xx.xx/30 (Cisco).
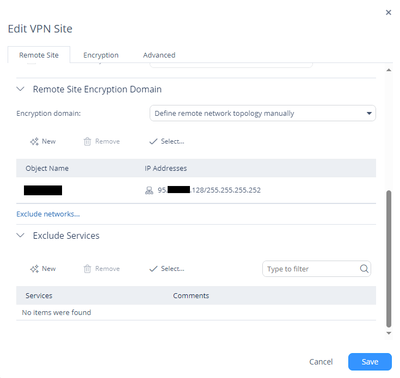
I added network 185.xx.xx.xx/29 to VPN->Site to Site -> Advanced -> Local ecryption domain is defined manualy...
But CheckPoint on Phase 2 sending traffic selector 0.0.0.0/0. Another firewall (PfSense, Strongswan, Huawei) normal to accept it. The problem is only with Cisco ASA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you show how you configured your VPN domain on CP side? The issue is, CP only sends 0.0.0.0/0 if the VPN domain is empty.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
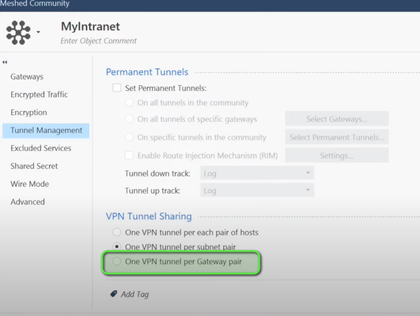
And i thought, it's defined in the tunnel management.
and now to something completely different - CCVS, CCAS, CCTE, CCCS, CCSM elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Config on screens:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In case you configured the domain to select it's proxy id per pair of gateways, it surely sends 0.0.0.0/0 what is expected behavior.
On the ASA side there should be something like this:
crypto map outside_map 10 match address VPN-Traffic
crypto map outside_map 10 set peer <Peer_IP_Address>
! Define the ACL for interesting traffic
access-list VPN-Traffic extended permit ip any4 any4
This is how i configured that long time ago
and now to something completely different - CCVS, CCAS, CCTE, CCCS, CCSM elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPSec is up if configure the following on the Cisco:
>>access-list VPN-Traffic extended permit ip any4 any4
But in this case, all traffic will be sent via IPSec.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just configure it as permanent tunnel using VTIs and set option @Vincent_Bacher advised in the community. I had done this many times and works without any issues. If you need help, just ping me.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to clarify the "one tunnel per gateway pair" is sometimes called "double quad zeroes" or a "universal tunnel" by some vendors if it helps locate their proper documentation for this setup.
Gateway Performance Optimization R81.20 Course
now available at maxpowerfirewalls.com
now available at maxpowerfirewalls.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Super valid point...I know Fortinet calls it that all the time, not sure about Cisco, but its probably the same thing.
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Interesting. I configured masses of VPN tunnels at FortiGate devices and never heard that wording 😄
and now to something completely different - CCVS, CCAS, CCTE, CCCS, CCSM elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now you have 😉
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 14 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 |
Trending Discussions
Upcoming Events
Thu 09 May 2024 @ 05:00 PM (CEST)
Under the Hood: Automate Azure Virtual WAN security deployments with TerraformThu 16 May 2024 @ 10:00 AM (CEST)
EMEA: Playblocks & MS Defender – Security Automation DeepDive into New Endpoint IntegrationThu 16 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - ACHTUNG, Sie werden gehackt! So schützen Sie sich!Thu 16 May 2024 @ 05:00 PM (CEST)
Americas: Playblocks & MS Defender – Security Automation DeepDive into New Endpoint IntegrationThu 16 May 2024 @ 04:00 PM (CEST)
CheckMates Live DACH - ACHTUNG, Sie werden gehackt! So schützen Sie sich!Fri 17 May 2024 @ 10:00 AM (CEST)
CheckMates Live Netherlands - Sessie 26: ElasticXL & VSNext DescriptionTue 21 May 2024 @ 10:00 AM (CEST)
CheckMates Live DACH - Einführung in Check Points Hyperscalinglösung - Quantum MaestroAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2024 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
Facts at a Glance
User Center